
It is a peculiar thing to see, but more and more commonly terms of art make their way into the mainstream media. It seems that every week a new article about a vulnerability, cyberattack, or data breach makes its way into public discourse. One phrase used to give confidence in a strong encryption scheme is “256-bit encryption”, but what does this mean?
- What is Encryption?
- What is a Key Size?
- How Strong is 256-bit Encryption?
- But what if the hardware gets better?
- Conclusion
What is Encryption?
Encryption is the practice of taking a message, referred to as “plain-text” and applying a series of transformations to produce “cipher-text”. This cipher-text is only readable by someone who can reverse this process, turning the cipher-text back into plain-text. Cipher-text is very portable – it can be safely sent via an insecure channel such as the internet without worrying about the contents of the message being intercepted by prying eyes. Broadly speaking, encryption falls into two major buckets: symmetric encryption, and asymmetric encryption.

Symmetric encryption refers to an encryption algorithm which relies on both parties being privy to the same encryption key – it is used both to encrypt and decrypt the message.
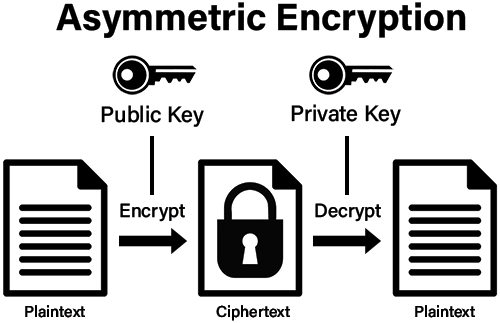
Asymmetric encryption on the other hand utilizes public/private keypairs. In this kind of encryption, both parties have a public key and a private key which are intrinsically, mathematically linked: that which can be encrypted via the public key can be reversed via the private key (and vice versa). Symmetric cryptography is much faster, but requires two parties to have communicated the key in advance via another channel. Asymmetric cryptography is slower, but can be performed without a prior exchange of information. SSL/TLS, the protocol most responsible for securing the internet, uses a mix of symmetric and asymmetric cryptography in order to get the best of both worlds.
What is a “Key Size”?
In cryptography, “key size” refers to the length of the secret key used to encrypt and decrypt information. If I asked you to pick a number 1 thru 4 (integers only!), you’d have a 25% chance of getting it right on your first try. If you got to pick 4 numbers, you’d have 100% chance of getting the right answer. In this way, if an attacker tries every possible key, they will eventually land upon the right one. This is referred to as a “brute force attack”. In order for something to be reasonably secure then, trying every possible key must be infeasible with modern hardware. But what is a bit? Instead of using our base-10 number system, computers rely on binary numbers because electrically, they operate on the presence or absence of current. These 1’s and 0’s are referred to as “bits”, and the number of them in your key is what defines your key-size. With a symmetric encryption key 256 bits long (2 to the 256th power possible combinations!), on current hardware it would take literally millions of years.
How Strong is 256-bit Encryption?
Given that it would take millions of years to try all possible combinations of an AES 256-bit key, what other attacks exist against modern encryption schemes? DES was rendered insecure to a 56-bit key size. As it turns out, not all AES is created equal! AES defines 5 different “modes”, some of which have suffered from rampant implementation flaws over the years. There is nothing preventing something we do not yet know from rendering many implementations of AES insecure in the same manner! Additionally, while infinitesimally unlikely, it is statistically possible for an attacker to guess the right key on the very first try! This is all to say that information security is relative, and it is fluid. AES 256-bit encryption represents the strongest symmetric encryption achievable today, but that is not a guarantee that this won’t change.
But what if the hardware gets better?
It will! over time, hardware improves. Some of you may be familiar with “Moore’s Law”, the tendency for the number of transistors packed into an integrated circuit to double every two years as we more and more clever with our manufacturing capabilities. Much in the same way, the computers of 2021 are staggeringly better than the computers of even as recent as 2005. Should this pace continue, it’s feasible that we eventually need to move away from current encryption methods. Many believe that quantum computing will rapidly accelerate this need. Quantum computers, unlike regular computers, are very good at reversing factorization of large prime numbers (the fact that this is so difficult is the very basis of RSA key generation). Luckily, alternative encryption algorithms already exist. But wait? You might ask, with baited breath. Why not move to those alternatives today? Why not pick keys so obscenely large that we never have to have this conversation again? Ultimately, the longer your key size, the more hardware time is needed to perform the encryption and decryption, and the more power the operation consumes. Ultimately, advances in battery technology have the potential to catapult us forward into uncharted terrain in terms of encryption. As constraints change, and as technology improves, optimizing for security and performance may look very different ten years from now, much like it looked very different ten years ago.
Conclusion
The next time you see them mention encryption in the news, try to figure out if they’re talking about symmetric or asymmetric cryptography. (If you’re wondering what length TLS keys are generally considered to be strong, asymmetric cryptography tends to require much larger key sizes such as 2048 or 4096 bit keys!). Try to determine how many attempts it would take to brute-force the key space. Consider what industry is being discussed and the tradeoffs the company must have made to arrive at the chosen key size (a bank is likely to use a larger key size and value future-proofing its security over performance.)
